Welcome to the wild and wacky world of online traffic ticket payments! In this article, we’ll dive deep into the mysterious realm of the NJMCdirect Payment Portal and uncover the secrets behind its security measures. So buckle up, dear reader, because we’re about to take a thrilling ride through the world of cyber safety and digital defenses. Get ready to decrypt the pixelated puzzles and crack the code of online payment security like never before!
Security Features of NJMCdirect Payment Portal
When it comes to online payments, security is key! Here at NJMCdirect Payment Portal, we take security very seriously. Our portal is equipped with top-of-the-line security features to ensure that your personal and payment information is always safe and secure.
So, what makes our payment portal so secure? Well, for starters, we use **industry-leading encryption** to protect your data. This means that all communication between your device and our servers is encrypted, making it virtually impossible for hackers to intercept your information.
But that’s not all – we also have **multi-factor authentication** in place to add an extra layer of security. This means that even if someone were to somehow get a hold of your login credentials, they still wouldn’t be able to access your account without verifying their identity through another method.
And if all else fails, we have a team of **cybersecurity experts** monitoring our portal 24/7 to ensure that any suspicious activity is detected and dealt with promptly. So rest assured, when you make a payment through NJMCdirect Payment Portal, your information is in good hands.
Encryption Protocols to Protect Personal Data
When it comes to protecting personal data, encryption protocols are the ultimate superheroes swooping in to save the day. These advanced algorithms make it nearly impossible for hackers to crack the code and access your sensitive information. But with so many options out there, it can be overwhelming to choose the right one. Fear not, dear reader, for I am here to break it down for you!
First up, we have Transport Layer Security (TLS). This protocol is like the bodyguard of the internet, ensuring that all communication between your device and the server is encrypted and secure. With TLS, your data is hidden behind layers of encryption, making it as elusive to cybercriminals as the Loch Ness Monster.
Next on the list is Internet Protocol Security (IPsec). This bad boy takes a no-nonsense approach to encryption, creating virtual private networks (VPNs) that cloak your data in an invisible forcefield. Think of IPsec as the secret agent of encryption protocols, silently protecting your data from prying eyes.
And last but certainly not least, we have Secure Sockets Layer (SSL). This protocol is the ninja warrior of encryption, stealthily encrypting the data as it travels between your browser and the server. With SSL, your personal information is guarded like a treasure chest full of gold doubloons, making it nearly impossible for hackers to lay their grubby hands on it.
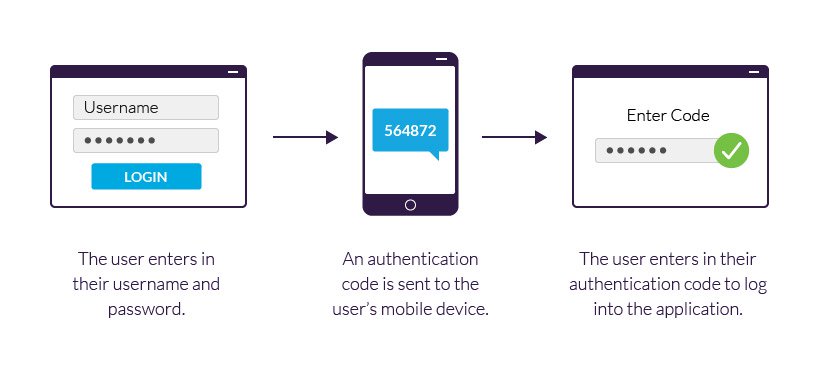
Two-Factor Authentication for Secure Access
So you think a simple password is enough to protect your sensitive information, huh? Well, think again! Two-factor authentication (2FA) is here to save the day and make your accounts extra secure.
With 2FA, you not only need to enter your password, but you also need to provide another piece of information to prove that you are who you say you are. This could be a fingerprint, a one-time code sent to your phone, or a security key. Hackers be warned – getting past a two-factor authentication is like trying to break into a bank vault with a toothpick!
So why bother with 2FA? Well, imagine this scenario: a hacker somehow gets a hold of your password (maybe you use ”password123″ – come on, you can do better than that!). Without 2FA, they can waltz right into your accounts and wreak havoc. But with 2FA, they’re stopped dead in their tracks, scratching their heads and wondering why they can’t access your precious data. Take that, hackers!
Don’t be lazy when it comes to securing your accounts. Enable two-factor authentication wherever you can and sleep soundly knowing that your information is locked up tighter than Fort Knox. Trust us, your future self will thank you when you don’t have to deal with the headache of a hacked account. Stay safe out there, cyber warriors!
Regular Security Audits to Identify Vulnerabilities
Security audits are like a surprise visit from your tech-savvy grandmother – she always seems to find something wrong with your cybersecurity setup, but it’s all for your own good!
During these audits, our expert team will meticulously sift through your digital drawers and cabinets to identify any potential vulnerabilities that could leave you open to cyber threats. It’s like playing a game of hide and seek with hackers, only we’re the ones doing the seeking!
Our audits cover everything from outdated software to weak passwords, ensuring that your defenses are as strong as a bodybuilder on leg day. We leave no digital stone unturned, leaving you with peace of mind knowing that your data is safe and sound.
So, don’t wait until your cybersecurity is as outdated as a pair of bell-bottoms - schedule a security audit today and let our team work their magic to keep your digital fortress secure!
24/7 Monitoring to Prevent Unauthorized Access
With our state-of-the-art security system in place, we are constantly vigilant to ensure that no unauthorized access occurs on our watch. Our team of highly trained professionals works tirelessly around the clock to monitor every inch of our premises, ready to pounce on any intruder who dares to step foot where they shouldn’t be.
Rest assured, we take our monitoring duties very seriously. You won’t catch us napping on the job, unless it’s a very well-deserved power nap after a long night of thwarting off potential threats. Our monitoring system is like a ninja in the shadows, silently watching over our property and ready to strike at a moment’s notice.
So whether it’s 3 AM or high noon, you can trust that our security team is on the ball, keeping watch and keeping our fortress safe from any would-be troublemakers. We don’t mess around when it comes to protecting our turf, and we’ll do whatever it takes to keep unauthorized access at bay.
PCI Compliance for Payment Card Security
So you’ve decided to dive into the world of , huh? Buckle up, because things are about to get real interesting!
First things first, let’s talk about the importance of PCI compliance. It’s like wearing a helmet when you ride a bike - sure, you might look a little dorky, but it could save you from a world of hurt (and fines) if you take a spill. Trust me, you don’t want to mess with those hefty non-compliance fees!
Now, navigating the world of PCI compliance can feel a bit like trying to untangle a slinky – frustrating and never-ending. But fear not! With a little bit of know-how and a whole lot of patience, you can conquer this beast. Just remember to dot your i’s and cross your t’s, because those sneaky hackers are always lurking around the corner.
And hey, if you ever start feeling overwhelmed, just take a deep breath and remember that you’re not alone in this journey. There are plenty of resources and experts out there ready to lend a helping hand. So chin up, my friend, and let’s tackle this PCI compliance monster head-on!
FAQs
How secure is the NJMCdirect Payment Portal?
Imagine Fort Knox, but with digital security. That’s how secure the NJMCdirect Payment Portal is. Your information is as safe as a momma bear protecting her cubs.
What measures does NJMCdirect take to ensure payment security?
NJMCdirect takes payment security very seriously. They use the latest encryption technology to protect your sensitive information. It’s like having your own personal bodyguard for your credit card details.
Is it safe to enter my credit card information on the NJMCdirect Payment Portal?
Absolutely! Entering your credit card information on the NJMCdirect Payment Portal is safer than hiding your snacks from your roommate. Your data is encrypted and stored securely, so you can pay your fines without a worry in the world.
What should I do if I notice any suspicious activity on my NJMCdirect account?
If you see something fishy on your NJMCdirect account, don’t panic! Contact their customer support team right away. They’ll investigate the issue faster than you can say “identity theft.”
Stay Secure, Stay Sane! 🛡️
And that’s a wrap on understanding NJMCdirect payment portal security! Remember, keeping your personal information safe is like protecting the last slice of pizza at a party - you don’t want anyone else getting their grubby little hands on it! So, follow the tips and tricks outlined in this article, and you’ll be navigating the NJMCdirect portal like a pro in no time. Happy paying (and staying secure)! 🤖🔒🌟